Maximize Business Performance with State-of-the-Art IT Solutions From Experienced Professionals
Maximize Business Performance with State-of-the-Art IT Solutions From Experienced Professionals
Blog Article
Discover the Important Sorts Of IT Managed Providers for Your Organization Demands
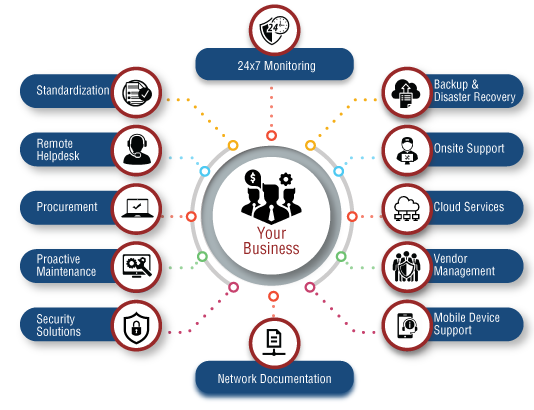
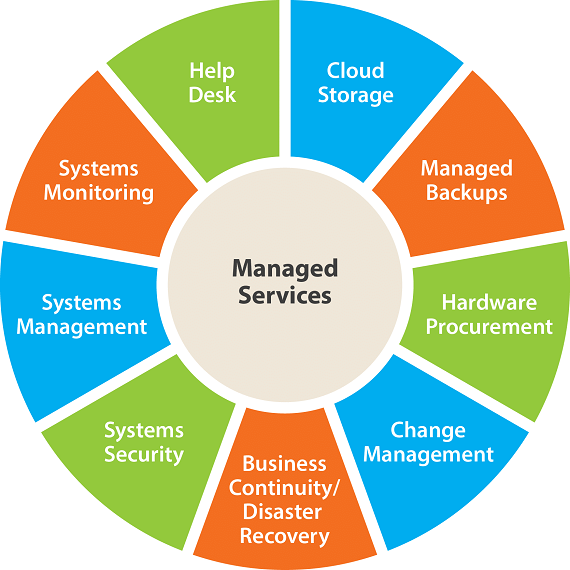
In today's quickly progressing technological landscape, understanding the necessary types of IT took care of solutions is essential for services looking for to enhance effectiveness and security. From network administration that ensures smooth connection to robust cybersecurity steps created to repel emerging hazards, each solution plays an unique role in bolstering business framework. Furthermore, cloud services and positive IT support can substantially affect operational dexterity. As we explore these services further, it ends up being obvious that straightening them with particular service demands is crucial for attaining ideal efficiency and development. What might this placement look like for your organization?
Network Administration Solutions
Network Administration Provider play a crucial function in guaranteeing the security and performance of an organization's IT infrastructure, as they incorporate an array of activities developed to monitor, preserve, and maximize network efficiency. These services are important for organizations that count heavily on their networks for day-to-day procedures, allowing smooth interaction and information transfer.
Trick parts of Network Monitoring Provider include network tracking, which tracks efficiency metrics and recognizes potential issues before they escalate into significant troubles. Aggressive monitoring makes sure that network resources are used efficiently, lessening downtime and improving performance. Furthermore, configuration administration is necessary for preserving optimum network settings, enabling fast adjustments in action to transforming service demands.
Additionally, protection monitoring within these services concentrates on securing the network from cyber threats, applying firewall softwares, invasion discovery systems, and regular security audits. This split method safeguards sensitive data and preserves governing compliance. Lastly, reporting and evaluation provide insights into network performance patterns, directing future facilities investments. By taking on comprehensive Network Administration Services, organizations can attain a durable and resilient IT environment that sustains their tactical objectives.
Cloud Computing Solutions
In today's electronic landscape, companies significantly transform to Cloud Computing Solutions to boost adaptability, scalability, and cost-efficiency in their IT operations. Cloud computing permits businesses to gain access to sources and services over the web, getting rid of the demand for extensive on-premises infrastructure. This shift results in significant financial savings on power, maintenance, and hardware expenses.
There are numerous types of cloud services readily available, consisting of Framework as a Solution (IaaS), Platform as a Solution (PaaS), and Software Application as a Solution (SaaS) IaaS provides virtualized computing sources, enabling organizations to scale their facilities based on demand.
In addition, cloud options promote collaboration among teams, as they can share and gain access to information flawlessly from different places. Additionally, cloud carriers frequently execute durable back-up and disaster healing options, additionally securing service connection. By leveraging Cloud Computing Solutions, organizations can not just enhance their IT resources yet additionally place themselves for advancement and development in a progressively competitive market.
Cybersecurity Solutions
Cybersecurity Providers have ended up being essential in guarding organizational information and infrastructure against an ever-evolving landscape of cyber dangers. IT services. As cybercriminals Check This Out continually establish extra sophisticated methods, organizations should execute robust safety and security actions to safeguard sensitive information and keep operational honesty
These solutions generally include a series of offerings such as risk evaluation and management, breach detection systems, firewalls, and endpoint defense. Organizations can gain from continual surveillance that recognizes and neutralizes potential threats before they intensify into serious breaches. Furthermore, cybersecurity solutions usually encompass worker training programs to promote a culture of security understanding, equipping personnel with the expertise to recognize phishing attempts and other destructive tasks.
Data Back-up and Healing
Data backup includes developing and keeping copies of vital information in protected places, guaranteeing that companies can recover info promptly in case of loss - managed IT provider. There are numerous back-up approaches readily available, consisting of full, step-by-step, and differential back-ups, each serving distinct demands and offering varying recuperation rates
In addition, businesses should take into consideration cloud-based back-up services, which provide scalability, remote access, and automated processes, reducing the concern on inner sources. Applying a detailed recovery strategy is similarly crucial; this plan should detail the actions for recovering data, consisting of screening recuperation refines consistently to guarantee efficiency.
IT Support and Helpdesk
Effective IT support and helpdesk solutions are crucial for maintaining operational connection within companies. These services work as the initial line of protection versus technological problems that can disrupt company functions. By supplying prompt aid, IT support teams enable employees to concentrate on their core obligations instead than grappling with technological challenges.
IT sustain includes a series of services, including troubleshooting, software program setup, and hardware upkeep. Helpdesk services usually involve a dedicated group that takes care of inquiries via various channels such as chat, email, or phone. The effectiveness of these services is usually measured by action and resolution times, with a focus on minimizing downtime and improving customer satisfaction.
In addition, a well-structured IT support group advertises positive trouble recognition and resolution, which can prevent small concerns from intensifying right into significant disturbances. Numerous organizations choose outsourced helpdesk services to take advantage of customized experience and 24/7 availability. This critical strategy permits companies to assign resources successfully while guaranteeing that their technical infrastructure stays robust and trusted.
Final Thought
Finally, the assimilation of important IT managed solutions, consisting of network management, cloud computer, cybersecurity, information page backup and recuperation, and IT support, considerably improves business effectiveness and security. managed IT provider. These services not only address certain organization needs yet additionally add to total operational continuity and growth. By purposefully leveraging these offerings, organizations can enhance their technical infrastructure, protect critical data, and make sure timely resolution of technical concerns, ultimately driving performance and promoting a competitive benefit in the marketplace
In today's quickly evolving technological landscape, comprehending the important types of IT handled solutions is essential for organizations looking for to improve efficiency and security. As we discover these solutions additionally, it ends up being apparent that aligning them with details business requirements is critical for achieving optimal performance and growth. Cloud computer allows businesses to gain access to resources and services over the internet, getting rid of the demand for considerable on-premises facilities.There are several kinds of cloud solutions offered, including Facilities as a Solution (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) These services not just address details service needs but likewise contribute to total functional connection and development.
Report this page